AWS IAM Errors
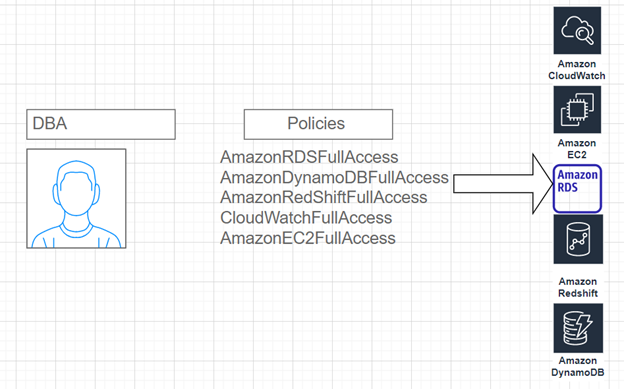
In this mini-project, I act as a system administrator who needs to up database administrators with the proper access permissions. To provide access and make sure the appropriate security measures are in place, I will use AWS Identity & Access Management (IAM) and attach the necessary AWS-managed policy that allows full access to Amazon Relational Database Service (RDS), DynamoDB, and RedShift.
What is IAM?
AWS Identity and Access Management (IAM) is a web service that helps you securely control access to AWS resources. With IAM, you can centrally control permissions that control which AWS resources users can gain access to. You use IAM to control who is authenticated (signed in) and authorized (has permissions) to use resources.
What is RDS?
Amazon Relational Database Service is a distributed relational database service by Amazon Web Services. It is a web service running "in the cloud" designed to make it easy to use a database.
What is RedShift?
Amazon Redshift is a data warehouse (primarily used for analytics) product and can handle large-scale amounts of data.
What is Dynamodb?
Amazon DynamoDB is a fully managed proprietary NoSQL (more flexible than RDS) database service that supports key–value and document data structures and is offered by Amazon.com as part of the Amazon Web Services portfolio.
Background on this mini project.
You need at least 2 IAM users to do this project. One user sets permissions and another user tests the permission. I will not go into detail about the creation of the permission policy. Let’s call the permission setting account the admin account and call the other account the dba account. A deep dive into what a dba is and aws database services are out of scope for this mini-project. This mini-project is focused on permissions.
Review Policy Permissions for DBAGroup as an Administrator.
1. I logged in with the admin account.
2. I navigated to the AWS Identity & Access Management service.
3. I then clicked on user groups and review my created permission policy.
4. When I created this policy, I gave dba account full access to cloudwatch and EC2.
5. I logged out with the admin account.
Try to use a Relational Database Instance, Redshift, and DynamoDB as a DBA
1. I then logged in with the dba account.
2. Then I went to the Amazon Relational Database Service (RDS)
3. Then I clicked on create a database, but that action failed because I don’t have the correct permissions.
4. When I navigated to redshift, I got this error.
5. When I tried to create a DynamoDB table I got this error.
6. Then I signed out of this account
Modify Permissions on the DBAGroup as an Administrator
1. Then I logged back in as the admin account.
2. Then I returned to my created permission policy.
3. Then I clicked on add permissions and then clicked on attach policies.
4. Next, I added the AmazonRDSFullAccess permission to my policy.
5. Next, I added full access permissions for Redshift, and DynamoDB as well.
6. Then I logged out again.
Verify Relational Database, Redshift, and DynamoDB Access as a DBA
1. Logged in with my dba account and now I have the correct permissions.
Additional security I could do.
1. Require MFA when Database Administrators log in.
2. Update the policies to not give full access to the requested services but give them just enough access to do their job.
3. Used conditions in the IAM policy I created to restrict more access.
4. Set up SSO for the users to log in.
5. Having a password complexity, and password expiration would make these users more secure as well.
What did I learn?
To summarize I was able to give the Database Administrators the correct permissions that they needed. I learned more about permission policies. The AWS-managed policies really are helpful when you are new to AWS. The policies are easy to read in JSON format as well. I feel like I gained a great deal of knowledge in this mini-project. Please see the link below to learn more about IAM best practices.